A couple of months ago, the popular tech blogger Linus Tech was hacked. All three of his YouTube channels (the biggest of which boasts over 15 million subscribers) fell into the hands of cybercriminals, who began broadcasting streams with crypto-scam ads. How did the hackers manage to gain access to the channels? Didn’t the famous tech-blogger protect his accounts with a strong password and two-factor authentication? Of course he did (at least, that’s what he himself says).
Linus Tech fell victim to a pass-the-cookie attack, a common method for targeting YouTubers. In this post we take a closer look at the objectives and motives behind such attacks, how hackers can access channels without knowing password and second factor, what Google’s doing about it, and how not to fall victim to this attack.
Why go after YouTube channels?
The channels of well-known (and not so well-known) YouTubers are usually taken over either to demand a ransom for their return, or to gain access to their audience (as in the hack on Linus Tech). In the latter case, after hacking the channel, the attackers change the name, profile picture, and content.
Thus, instead of a blog, say, about tech innovation, there appears a channel that imitates the account of some large company (most often Tesla) with the corresponding profile picture. After that, the attackers use it to stream recordings of Elon Musk expressing his thoughts about cryptocurrency. All other blog content is often removed.
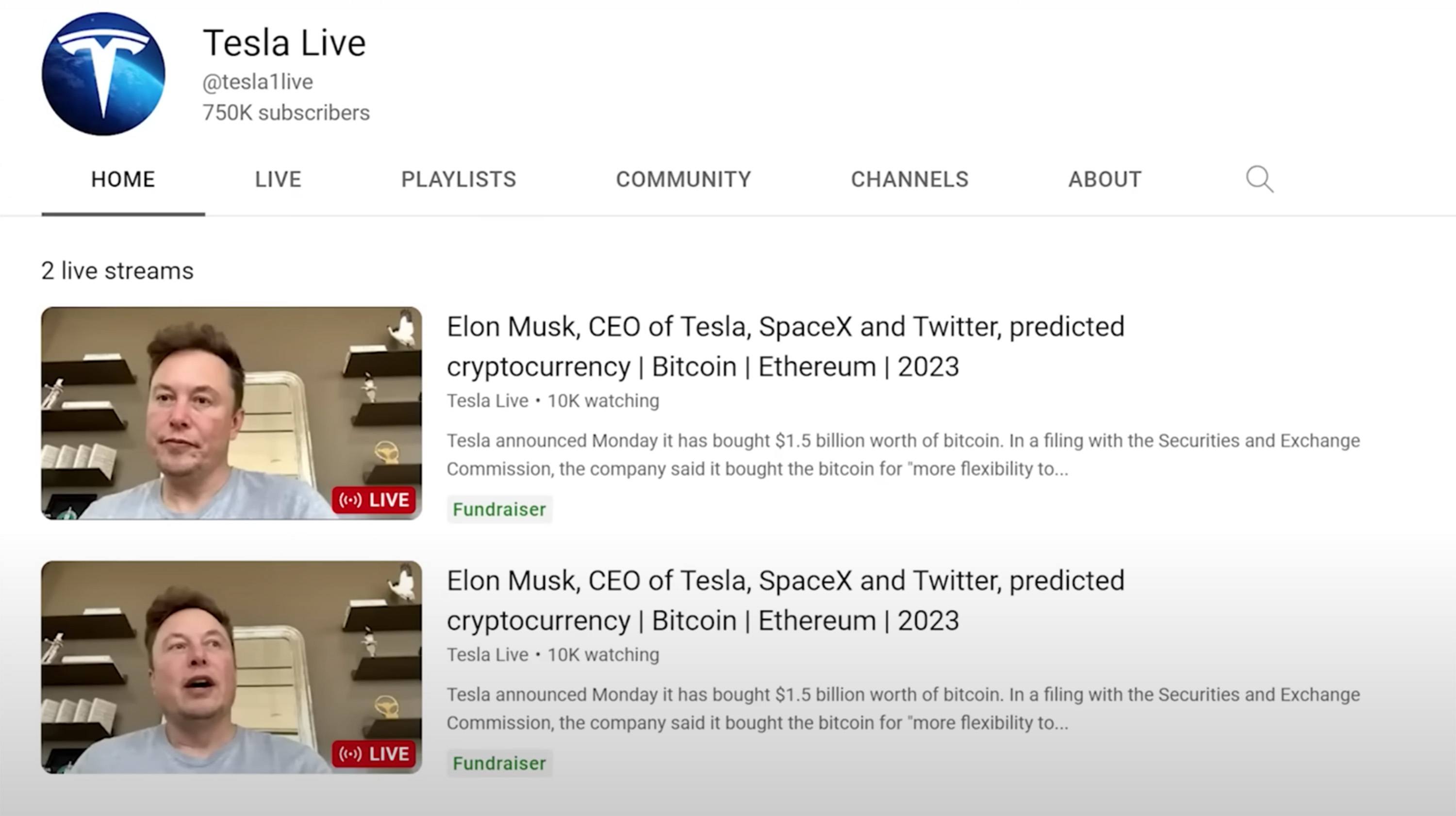
Streams with Elon Musk on a hacked channel. Source
At the same time, a link to a site of a “unique cryptocurrency promotion” is dropped into the chat. For example, Musk himself is supposedly giving away cryptocurrency: to get their share, users are asked to transfer their coins to a certain wallet, after which they will get back twice as much.

Streams with Elon Musk on a hacked channel. Source
A curious detail: scammers often have the foresight to set restrictions in the chat: only users who’ve subscribed to the channel for more than 15 or even 20 years can post messages (and it doesn’t matter that not only this channel didn’t exist then, but YouTube itself only appeared in 2005).
Sure, this is an example of a typical scam we’ve analyzed once or twice before.

Transfer your bitcoins to us and we’ll give you back twice as many. Source
The stream is quickly blocked by YouTube, along with the unfortunate blogger’s channel, for “violating YouTube’s Community Guidelines”. And then the real owner faces the absorbing task of restoring their own channel and proving to the platform that it was not they who distributed links to fake sites and streamed scam ads.
In the case of Linus Tech, with his 15 million subscribers, this was relatively easy to do. His channel was restored within hours, though he did lose that day’s monetization. How long a YouTuber with a smaller audience would need to rectify the situation, and whether it would be possible at all, are questions you don’t want to get an answer to from your personal experience.
Hijacking a channel without the password
To hack a YouTube channel, there’s no need for attackers to steal any credentials. Getting their hands on session tokens will suffice. But first things first…
A typical attack on a YouTube channel begins with an email to the blogger seemingly from a genuine company proposing collaboration; this can be a VPN service, a game developer or even an antivirus vendor. There’s nothing suspicious in the first email, so the member of the blogger’s team replies with a standard message detailing their product placement fees.
The next email is far less innocent. In it, the scammers send an archive supposedly containing a contract, or a link to a cloud service to download it, as well as the password for this archive. To make the email more convincing, the attackers often add a link to a website or social network account affiliated with the product they want the blogger to “promote”. The link can point either to the site of a bona fide company, or to a fake page.
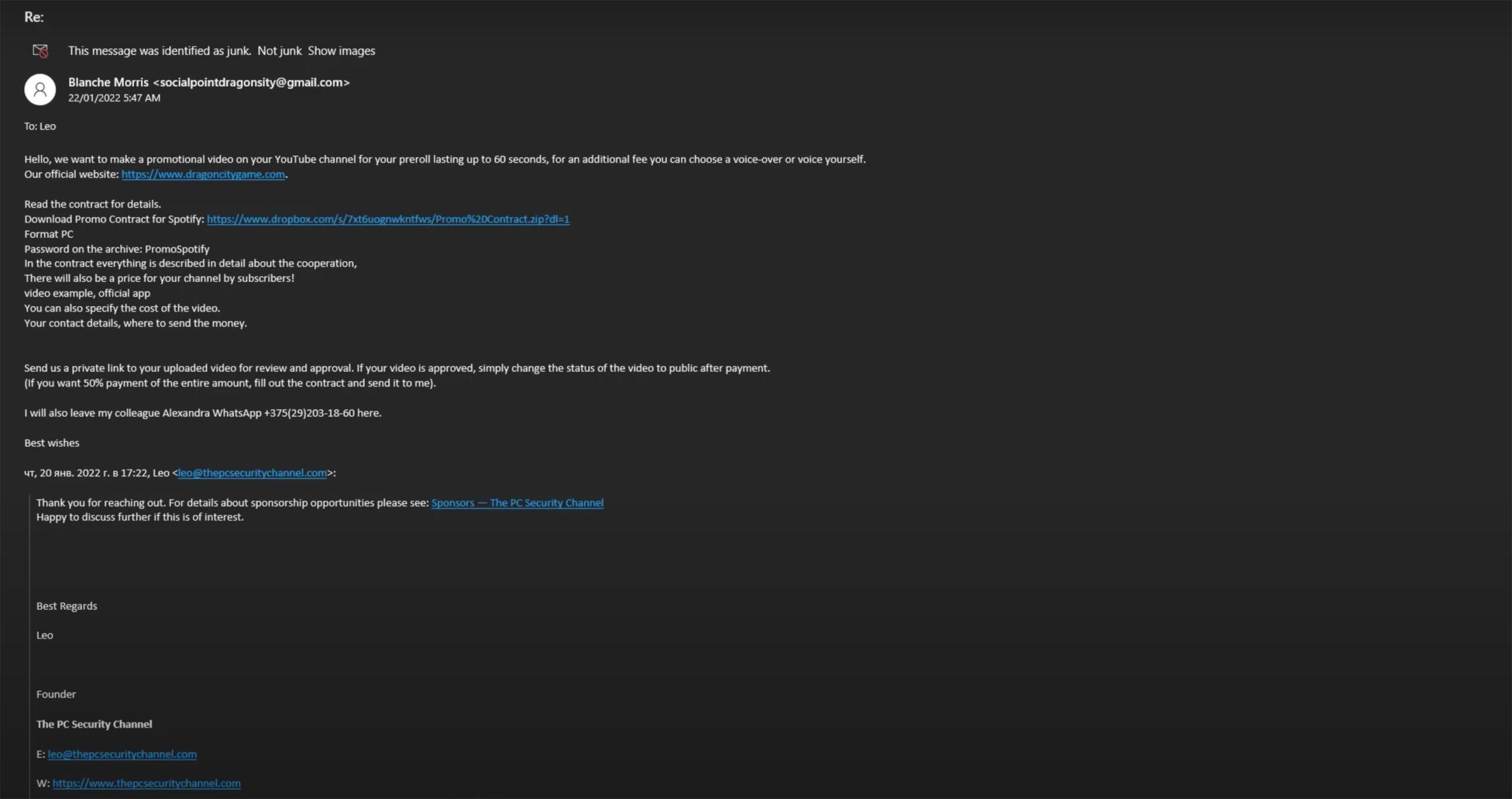
Email with a link to download an archive with a “contract”. Source
If the blogger or their employee is not careful and unzips the archive, they’ll find one or more documents that may look like regular Word or PDF files. The only odd thing is that all the files are quite large (more than 700MB), which makes it impossible to scan them for threats using a service like VirusTotal. Many security solutions will skip them for the same reason. Opening the files with special tools for analyzing executables reveals the presence of very many empty spaces, which is what makes these documents so big.
Of course, hiding inside the file that looks like an innocent contract is a whole host of malware. Aware of the problem, Google analyzed such attacks and identified the various types of malware used. Among them was the RedLine Trojan stealer, which has been blamed by many YouTubers for their misfortunes lately.
Attackers use this malware to achieve their main aim of stealing session tokens from the victim’s browser. With the help of session tokens or cookies, the browser “remembers” the user, allowing them to avoid going through the full authentication process each time with a password and second factor. That is, stolen tokens let cybercriminals impersonate authenticated victims and log in to their accounts without the credentials.
What about Google?
Google has been aware of the problem since 2019. In 2021, the company published a major study entitled Phishing campaign targets YouTube creators with cookie theft malware. Google’s Threat Analysis Group investigated the social engineering techniques and malware deployed in such attacks.
Following the study, the company announced it had taken a number of steps to protect users:
- Extra heuristic guidelines were implemented to identify and prevent phishing and social engineering emails, cookie theft hijacking, and fraudulent cryptocurrency livestreams.
- Safe Browsing now includes enhanced capabilities to identify and block malicious webpages and downloads.
- YouTube has strengthened the processes involved in transferring channels, and successfully detecting and automatically recovering more than 99% of compromised channels.
- Account Security has reinforced the authentication procedures to prevent and alert users about potentially risky activities.
Are these measures working? Judging by the comments of YouTubers themselves, and the fact that such hacks continue to occur regularly (when writing this post, I myself found Elon Musk streams on three evidently stolen channels) — not really. That same Linus Tech was outraged that, in order to change the name of the channel and its profile picture and also remove all videos from the channel, YouTube does not ask the user to enter a password or second factor code.
Protect your channel yourself
In order not to lose control over your own channel, it’s wise to take a number of precautions. First of all, install reliable protection on all work devices and hold regular team trainings in cybersecurity. Everyone with access to business accounts must:
- Know the typical signs of phishing
- Be able to identify social engineering
- Never follow suspicious links
- Never download or open archived attachments from untrusted sources.
 scam
scam

 Tips
Tips