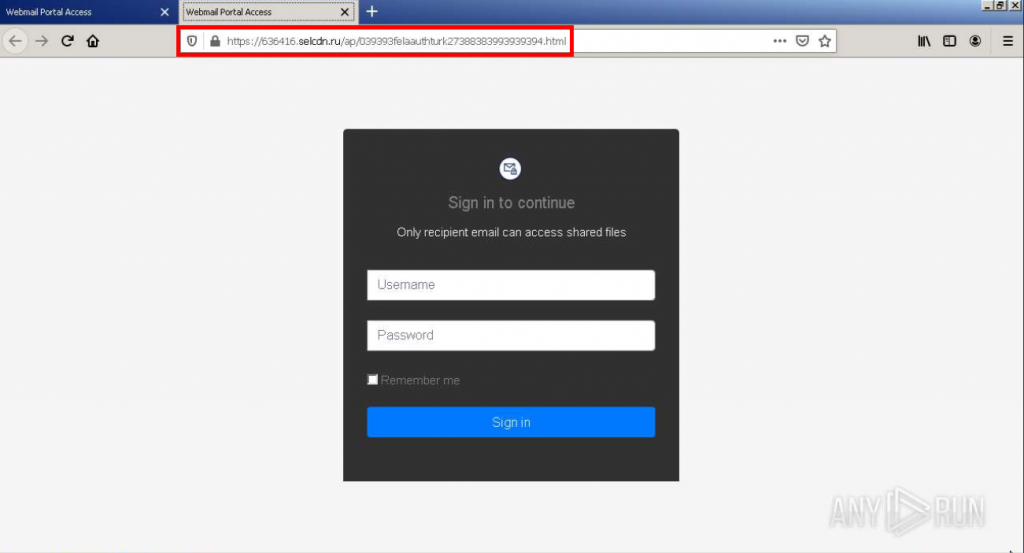
Bypass phishing detections with Google Translate
A new wave of phishing is currently circulating (a related story from derstandard.at newspaper can be found here). Documents are said to have been sent to you from a scanner, which you can allegedly download, as can be seen in the following image.
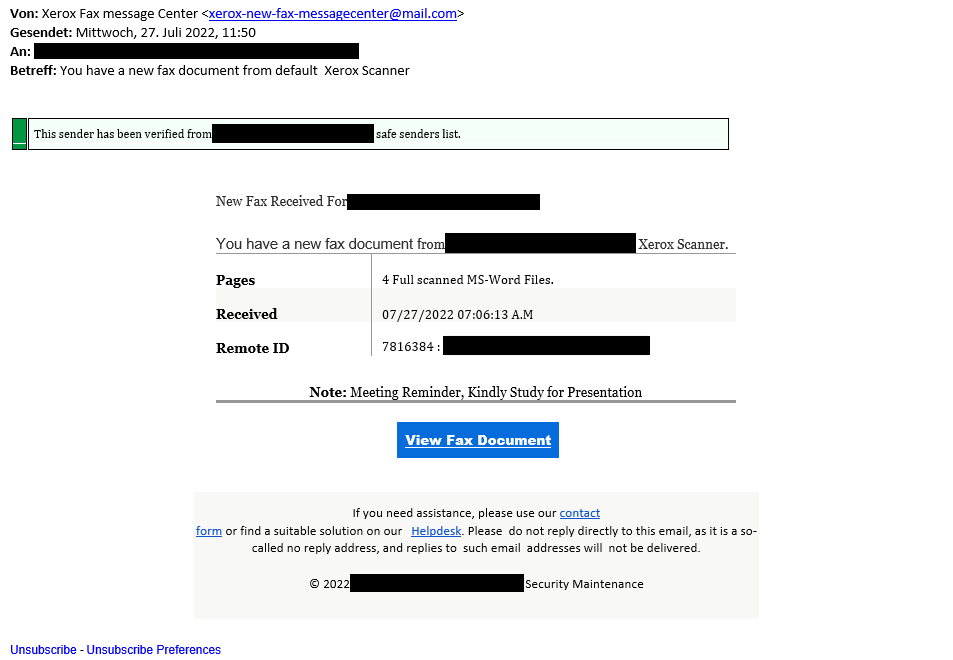
The first thing that is interesting is the green bar, which is intended to make the victim believe that the sender is already in their own list of trustworthy senders. However, such a list usually does not exist in this form – it is merely trying to psychologically suggest to the potential victim that the mail is harmless.
Sendgrid is used to send the emails and also to disguise the links they contain. This is one of the more well-known platforms for the delivery of e.g. legitimate marketing mails and is therefore classified as trustworthy by most mail filters from the outset. The links in the e-mail are also automatically replaced by Sendgrid with their own. When you click on the links, the browser first takes you to the legitimate Sendgrid domain and from there you are immediately directed to the actual target URL. This further increases the chances of such phishing mails being delivered.
The actual URL to which the mail delivery service Sendgrid is forwarded is again an obfuscation step. The attacker tries to trick even more complex mail filters that also check forwarding. To do this, it uses the Google Translate translation service in the form “https[:]//ATTACKER-URL.translate.goog” to present a phishing page to the potential victim. The site remains functional for the attacker, but is recognized as a trustworthy Google domain in various filters and other protective devices.
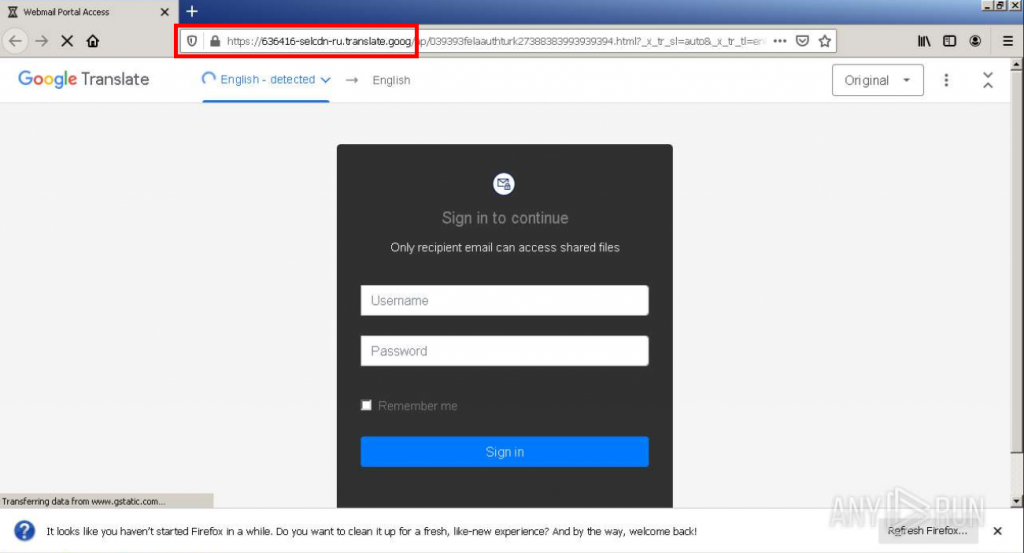
An analysis of the page embedded in Google Translate leads to a Russian domain (see below). When called up, connections are also established to other domains and IPs classified as dangerous, which, for example, have already been used to communicate with known malware. To protect against potential infections, it is therefore recommended not only not to enter any access data, but also not to click on the links in the first place.