Variant Cloud Analysis
Another yet quick blog post.
A few years ago, 3 or 4, maybe 5, I was "working" with @marcioalm in a "Simple Web Vulnerability Scanner" tool intended to be part of an automation vulnerability check for a large and specific environment.
Keep in mind that adventure was before the release of the well-acclaimed Nuclei, and Nuclei, since its first releases implemented better features than our tool. By the way, the tool was/is named Stryker.
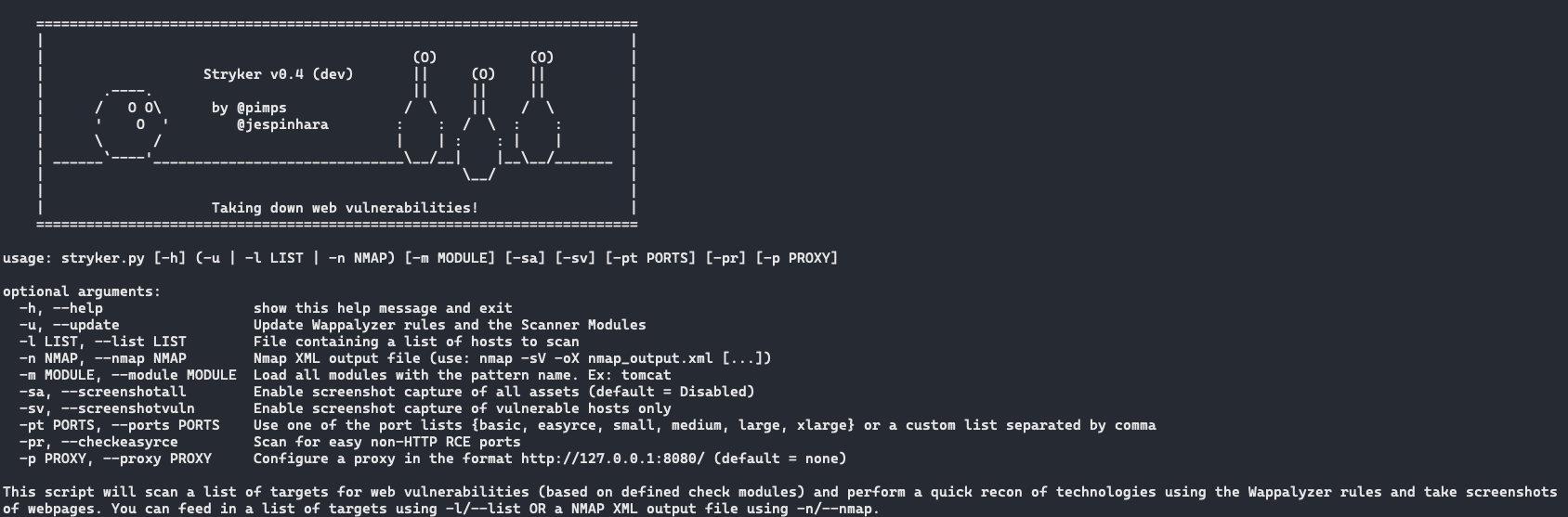
The idea behind the Stryker was quite simple, read a JSON file, aka "Stryker module", build the request then parse the response.
Stryker modules are simple to write; for example, a simple check for the CVE-2017-9506.
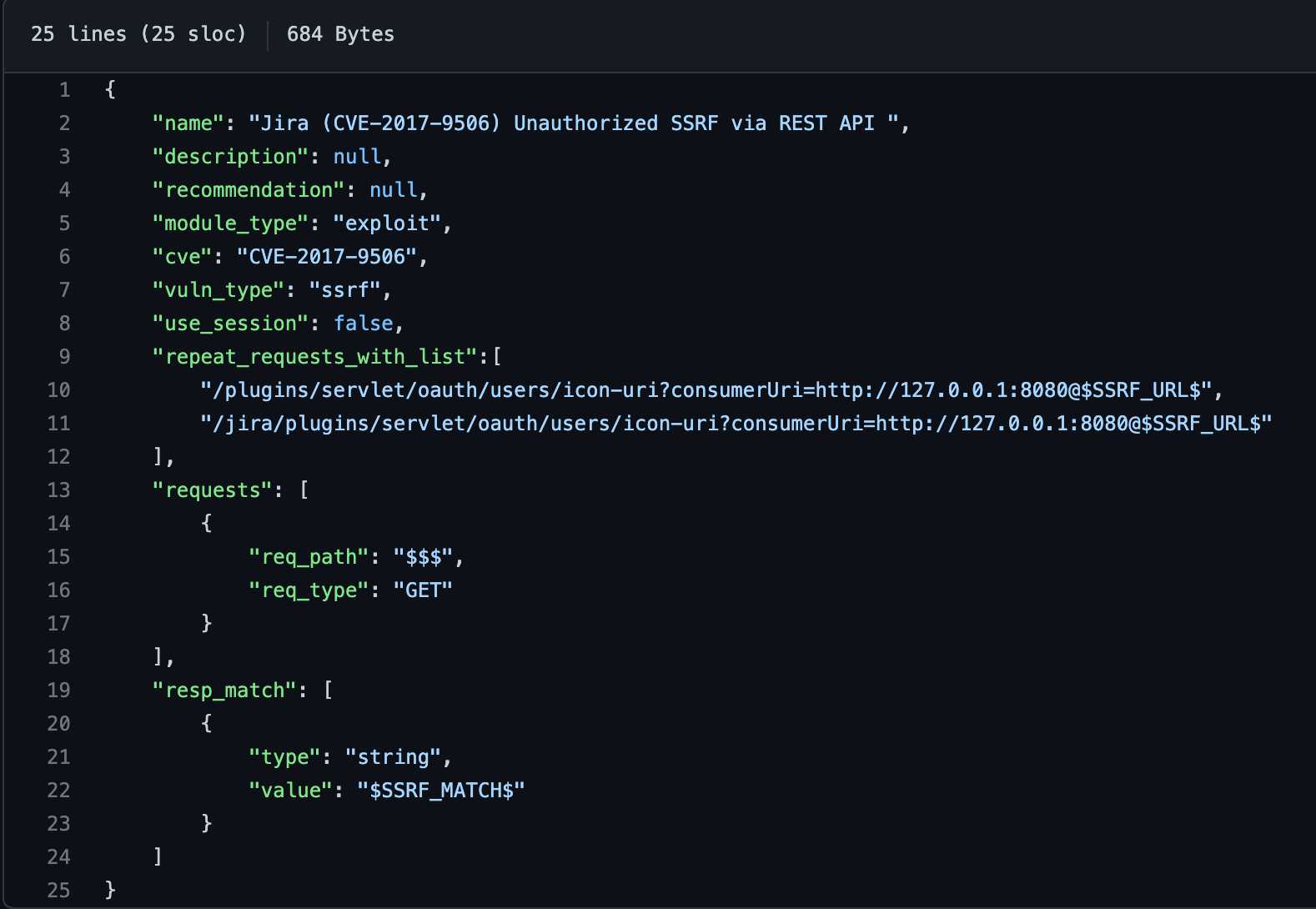
As I said before, nowadays, Stryke is outdated, and for us, it was well replaced by Nuclei.
So, what is the relation between Stryker and Variant Cloud Analysis?
Back in those days, Stryker was getting good results against the organization we were testing. Then I had the idea to test against a well tested Bug Bounty program scope.
The Variant Cloud Analysis (VCA) term was coined (?) (probably there is another name for this same thing running for ages in the industry) when we started to observe different results when running Stryker against the same bug bounty program scope many times using different:
- Cloud providers
- Instances types
- Regions
For transparency, almost tests were performed using Amazon AWS as the cloud provider.
The most exciting finding was testing for Apache Tomcat Manager Default Password on a public and well-tested Bug Bounty Program. We got one hit, which was 100% unexpected since I believe people constantly scan this kind of issue.
As expected, I did submit a report using the HackerOne platform.
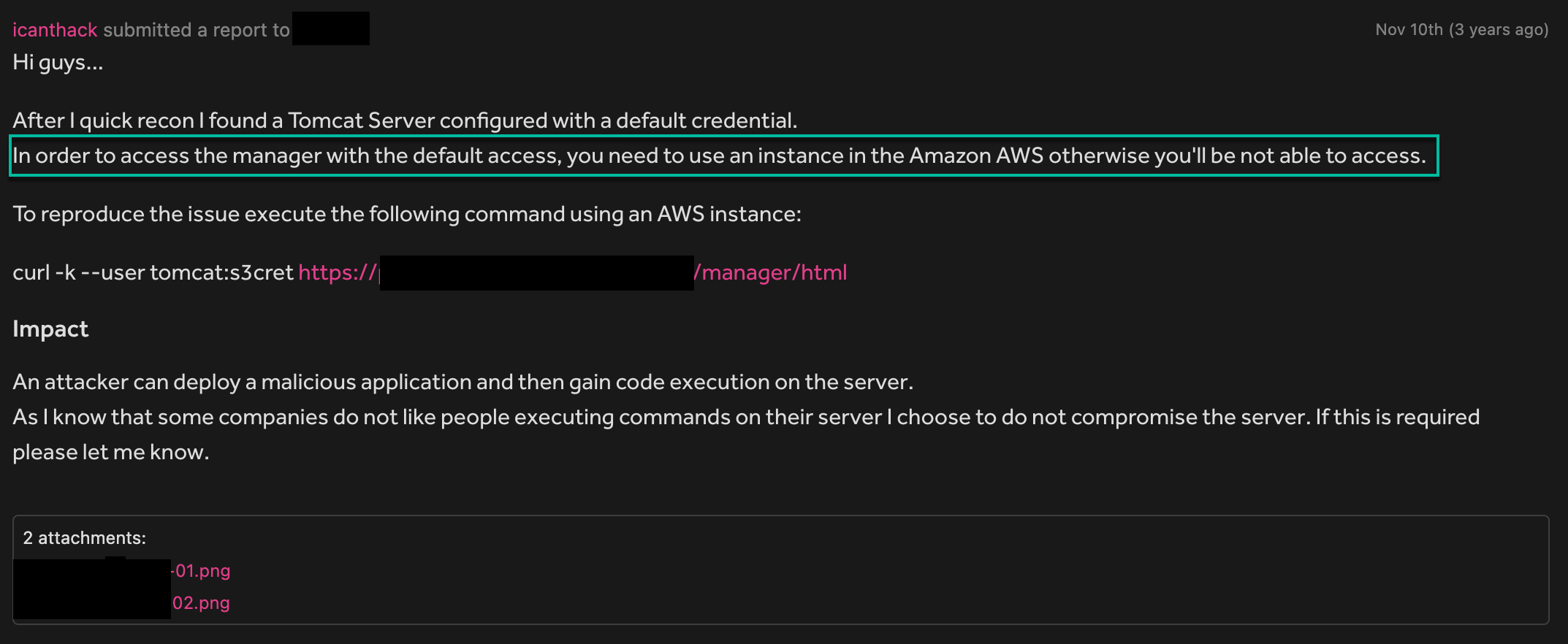
Triage returned, saying it was unable to reproduce the report.
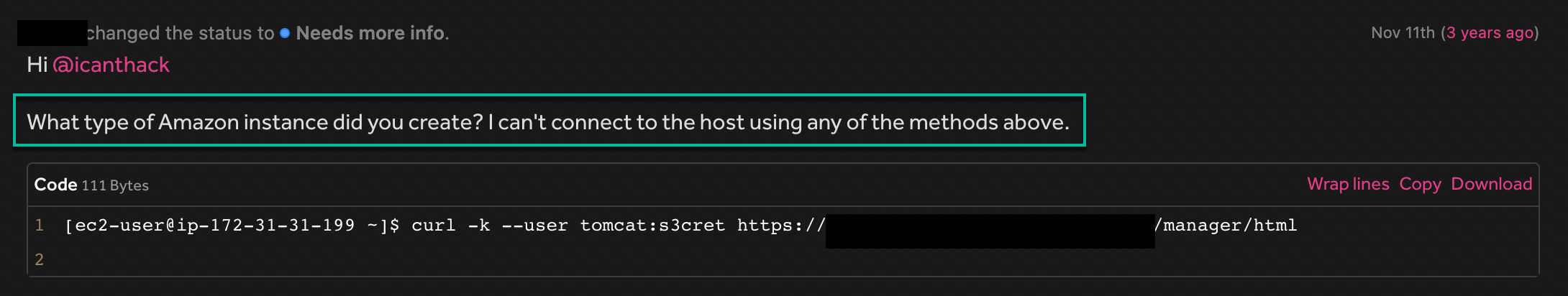
My fault. I did not provide all the information necessary. To reproduce the report, it was required to use an AWS instance type t2.xlarge in the us-east-1a region.
As a result, the report was closed, and the bounty was only used to pay for the AWS adventure bill. :)

The takeaway from this short and hard to read blog post is when running your recon/scanning/automation, try tricks such as:
- Different Cloud Providers
- As many regions as possible
- Different Instance Types
- Automation is the key
There is no link to Stryker since it is pretty much dead. Use Nuclei instead.
Cya...
