
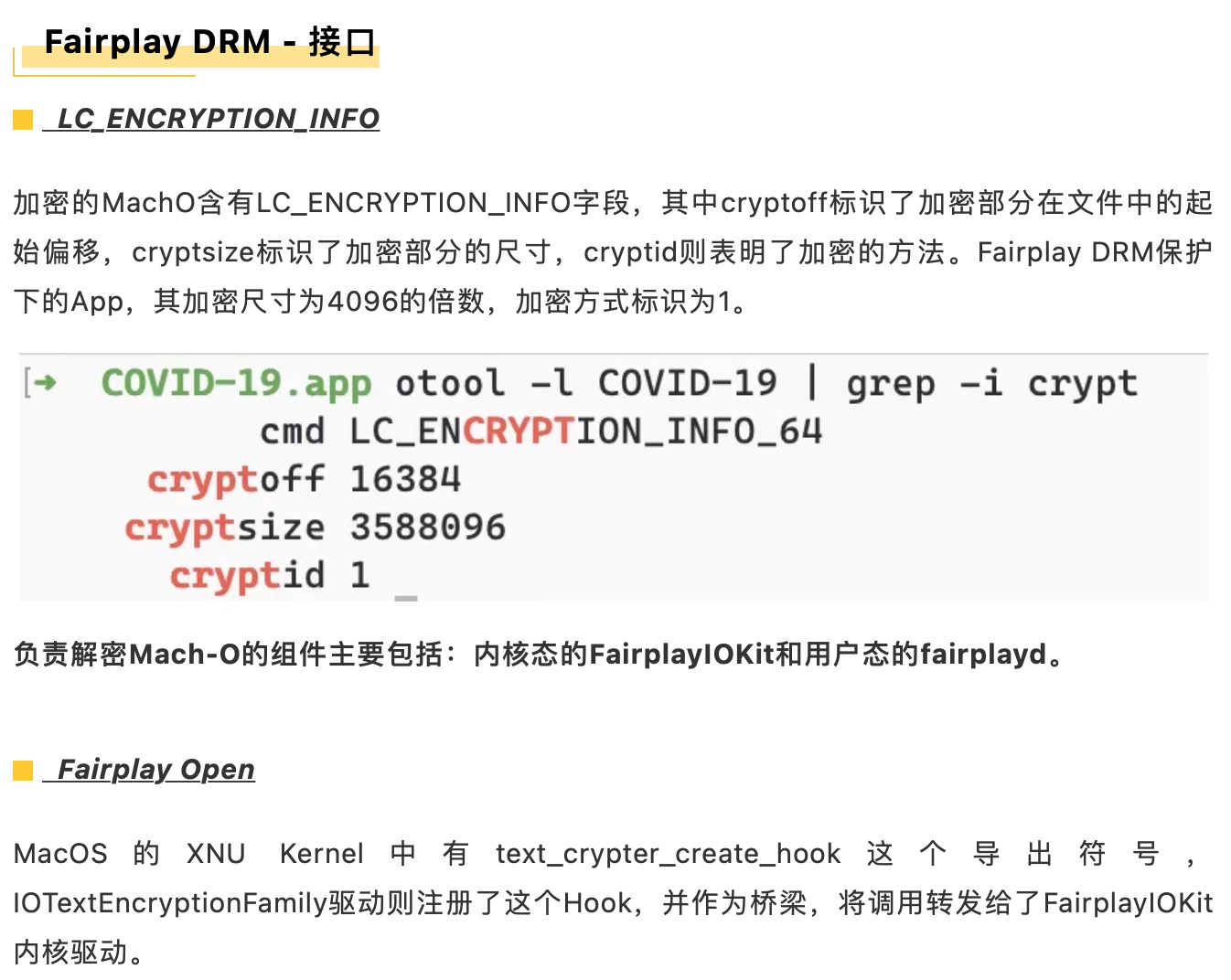
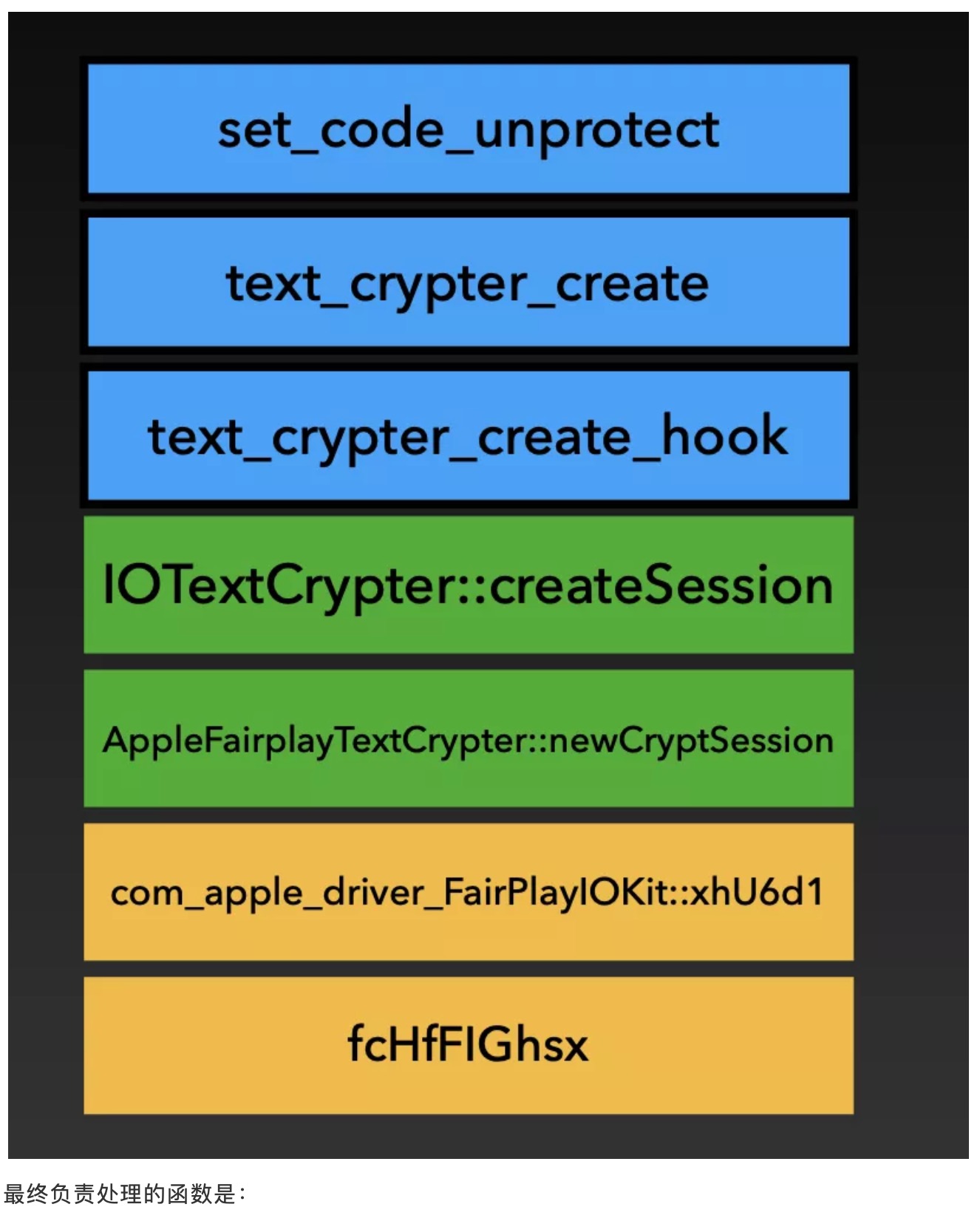
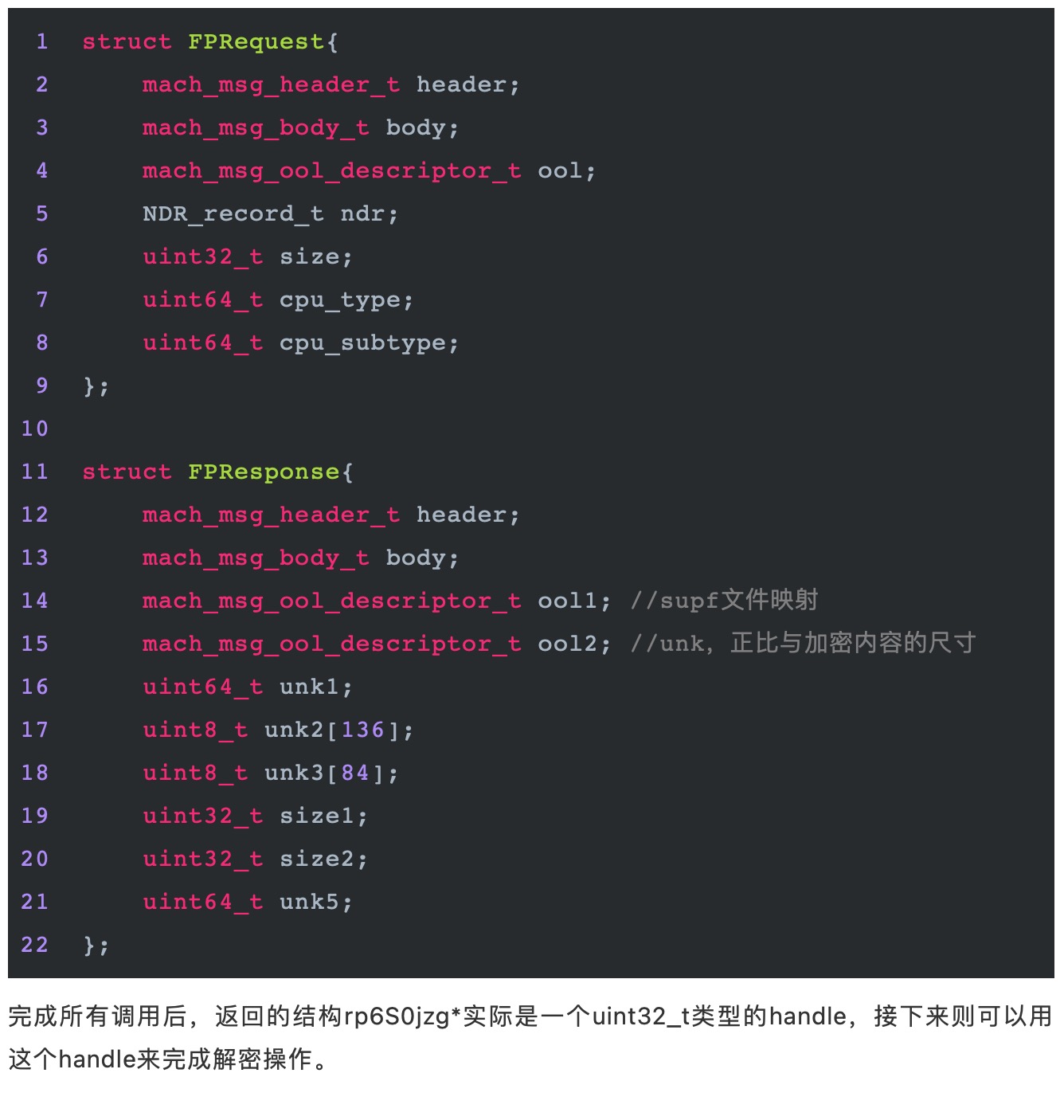
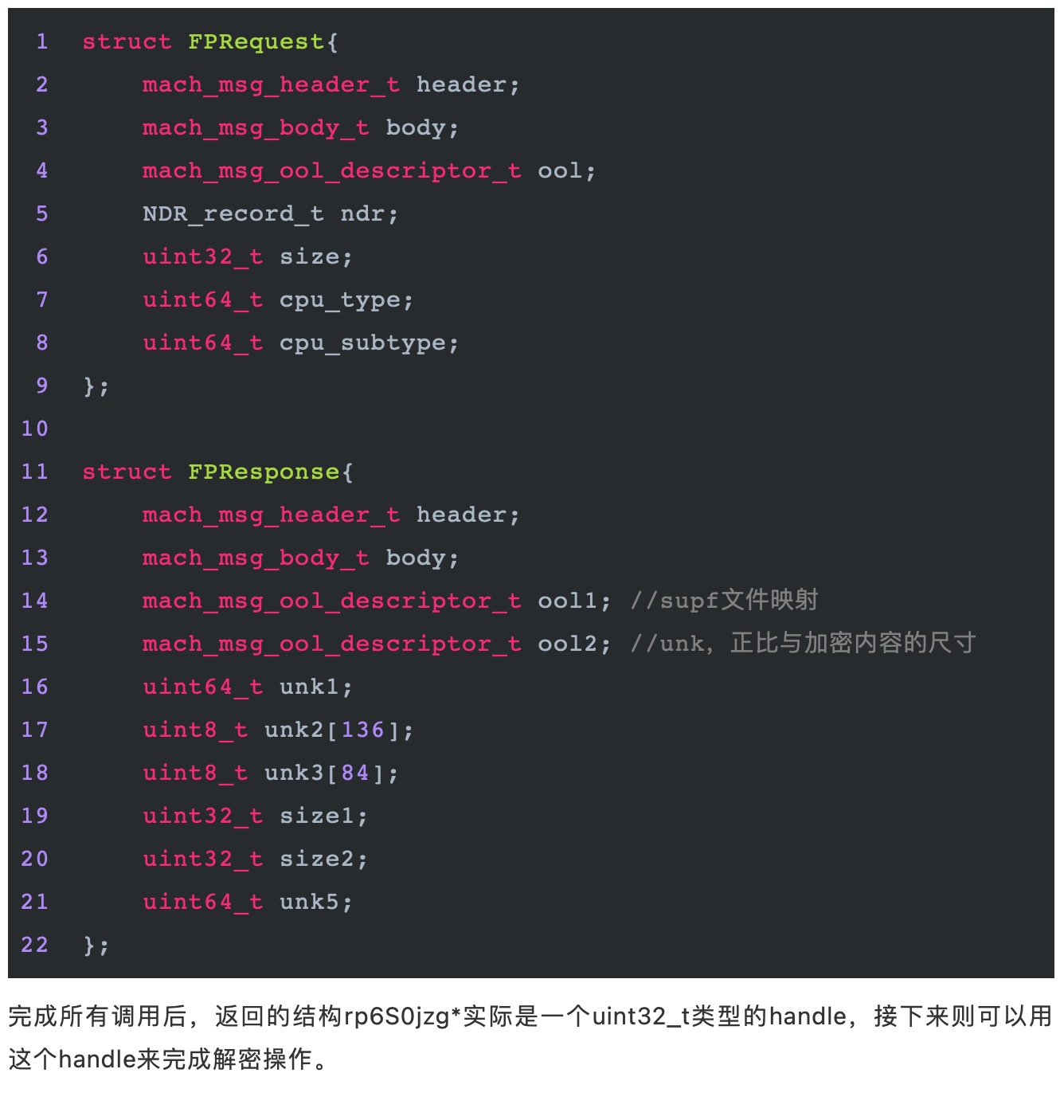
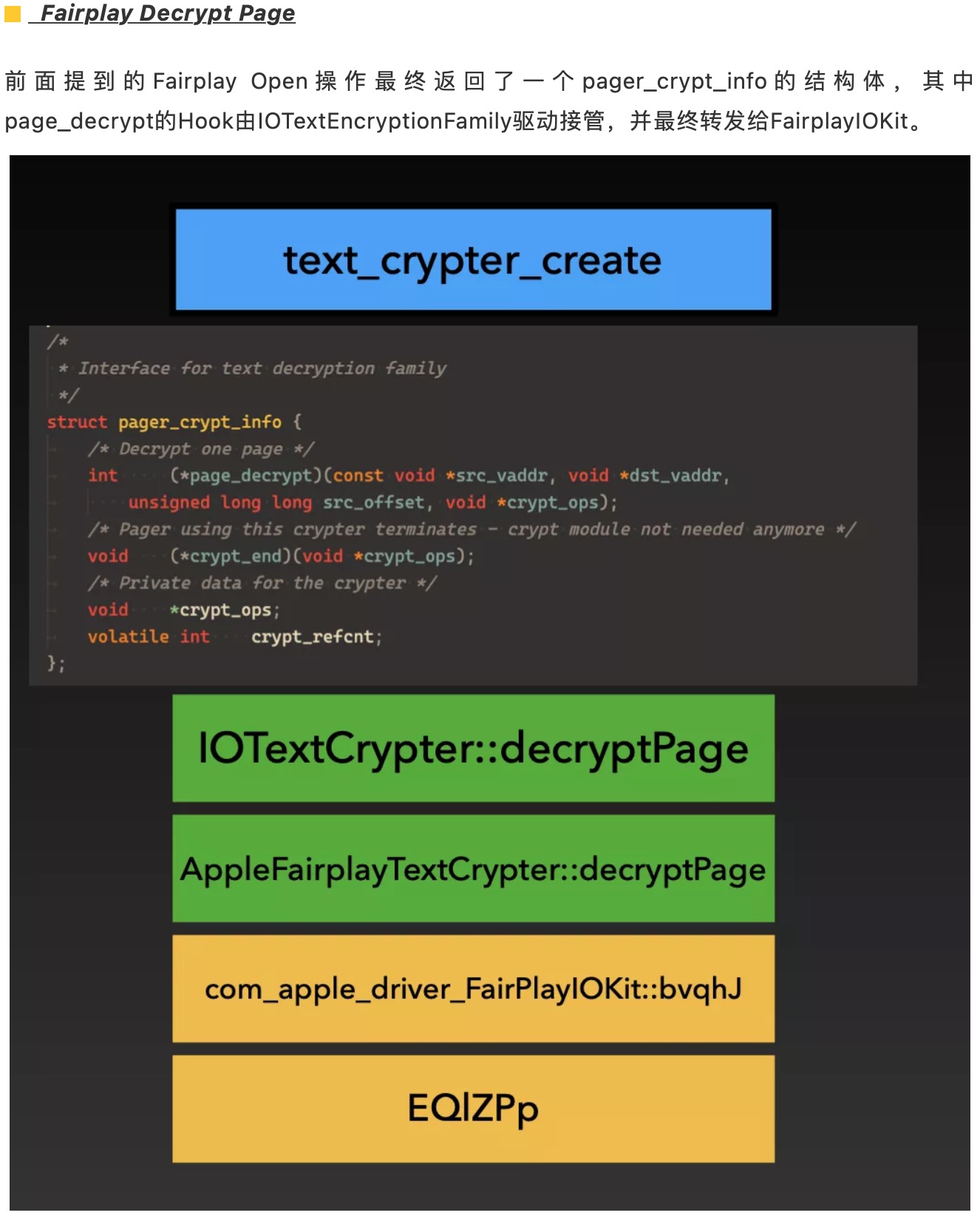
1KeyPair Segments:
2 Segment 0x0: arm64, Keys: 0x36c/4k, sha1sum = e369546960d805dd1188d42e3350430c7e3a0025
3
4Fairplay Certificate:
5 Data:
6 Version: 3 (0x2)
7 Serial Number:
8 33:33:af:08:07:08:af:00:01:af:00:00:10
9 Signature Algorithm: sha1WithRSAEncryption
10 Issuer: C=US, O=Apple Inc., OU=Apple Certification Authority, CN=Apple FairPlay Certification Authority
11 Validity
12 Not Before: Jul 8 00:48:29 2008 GMT
13 Not After : Jul 7 00:48:29 2013 GMT
14 Subject: C=US, O=Apple Inc., OU=Apple FairPlay, CN=AP.3333AF080708AF0001AF000010
15 Subject Public Key Info:
16 Public Key Algorithm: rsaEncryption
17 RSA Public-Key: (1024 bit)
18 Modulus:
19 00:b0:01:16:4b:62:b2:37:8d:60:12:4f:02:15:15:
20 a0:32:1b:e8:ed:44:ed:e9:17:5b:ec:9e:5d:11:24:
21 5a:66:2f:dc:a3:25:aa:52:70:e1:09:22:09:4b:65:
22 0f:67:f5:82:dc:af:78:9b:4c:45:f3:b4:f4:77:aa:
23 fc:a3:b2:84:c3:8b:09:c6:2e:55:f5:14:85:07:ac:
24 ae:0d:ff:ff:ca:41:3b:44:cb:52:b6:28:60:55:23:
25 35:8d:26:71:c6:12:a5:e0:72:58:09:3c:4a:9e:b6:
26 63:df:2a:91:94:27:eb:65:0a:b2:36:45:11:c1:91:
27 43:58:12:d9:e5:18:a1:ad:db
28 Exponent: 65537 (0x10001)
29 X509v3 extensions:
30 X509v3 Key Usage: critical
31 Digital Signature, Key Encipherment, Data Encipherment, Key Agreement
32 X509v3 Basic Constraints: critical
33 CA:FALSE
34 X509v3 Subject Key Identifier:
35 7B:07:34:81:A5:75:D0:F6:11:BB:D2:36:3F:79:93:4B:A1:70:EB:CF
36 X509v3 Authority Key Identifier:
37 keyid:FA:0D:D4:11:91:1B:E6:B2:4E:1E:06:49:94:11:DD:63:62:07:59:64
38
39 Signature Algorithm: sha1WithRSAEncryption
40 06:11:4e:87:ed:b1:08:70:c2:0d:e4:d2:94:bb:7f:ee:50:18:
41 c0:2a:21:34:0e:99:1f:bf:60:a2:58:d0:0c:28:3d:03:5b:ab:
42 4e:72:69:ba:41:52:45:b2:29:27:4a:c8:ba:7f:b5:9b:63:78:
43 b1:68:41:40:59:3f:05:8a:57:74:c5:63:30:cc:f3:20:41:c0:
44 3c:65:d4:0d:22:47:f3:97:76:e6:d6:3c:eb:e7:20:78:10:59:
45 fd:96:09:82:c3:41:f0:5f:d0:3e:91:44:6d:77:3f:a5:d9:da:
46 f0:f7:53:ad:94:61:28:1c:4c:40:3b:17:2b:dd:e3:00:df:77:
47 71:22
48
49RSA Signature: 6aeb00124d62f75f5761f7c26ec866a061f0776be7e84bfad4b6a1941dbddfdb3bd1afdcc5ef305877fa5bee41caa37b1a9d4ce763cf7d2cb89efa60660a49dd5ddff0f46eee7cd916d382f727d912e82b6e0a62e8110c195e298481aa8c8162faac066ef017c6c2c508700d7adb57e0c988af437621e698946da1b09adf89e9

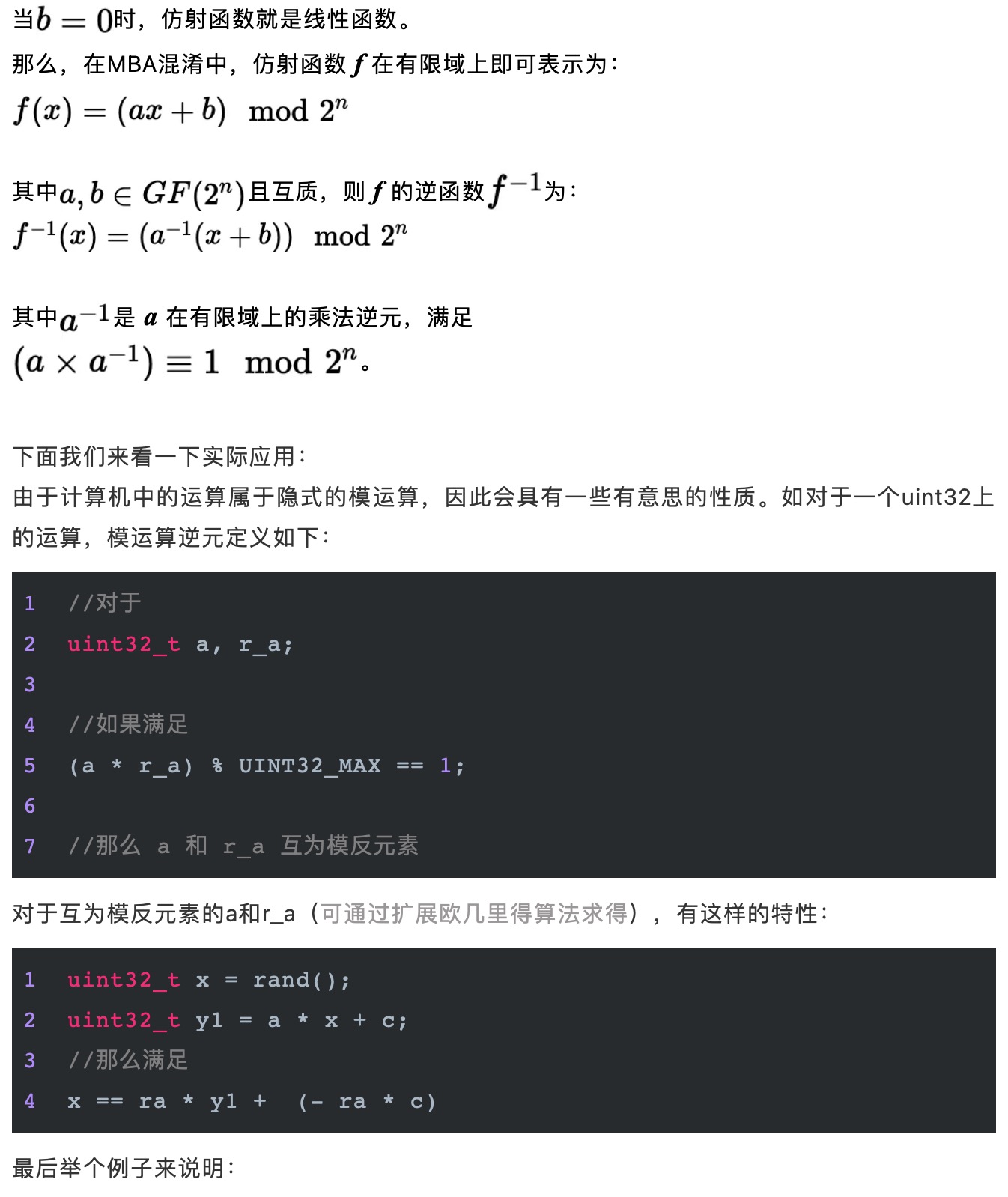
1//对于互为模反元素的4872655123 * 3980501275,取
2uint32_t x = 0xdeadbeef;
3uint32_t c = 0xbeefbeef;
4//则 -ra * c = 0x57f38dcb,且
5((x * 4872655123) + 0xbeefbeef) * 3980501275 + 0x57f38dcb == x
6/*
7可在lldb中验证如下
8(lldb) p/x uint32_t x=0xdeadbeef; (uint32_t)(((x * 4872655123) + 0xbeefbeef) * 3980501275 + 0x57f38dcb)
9(uint32_t) $8 = 0xdeadbeef
10*/
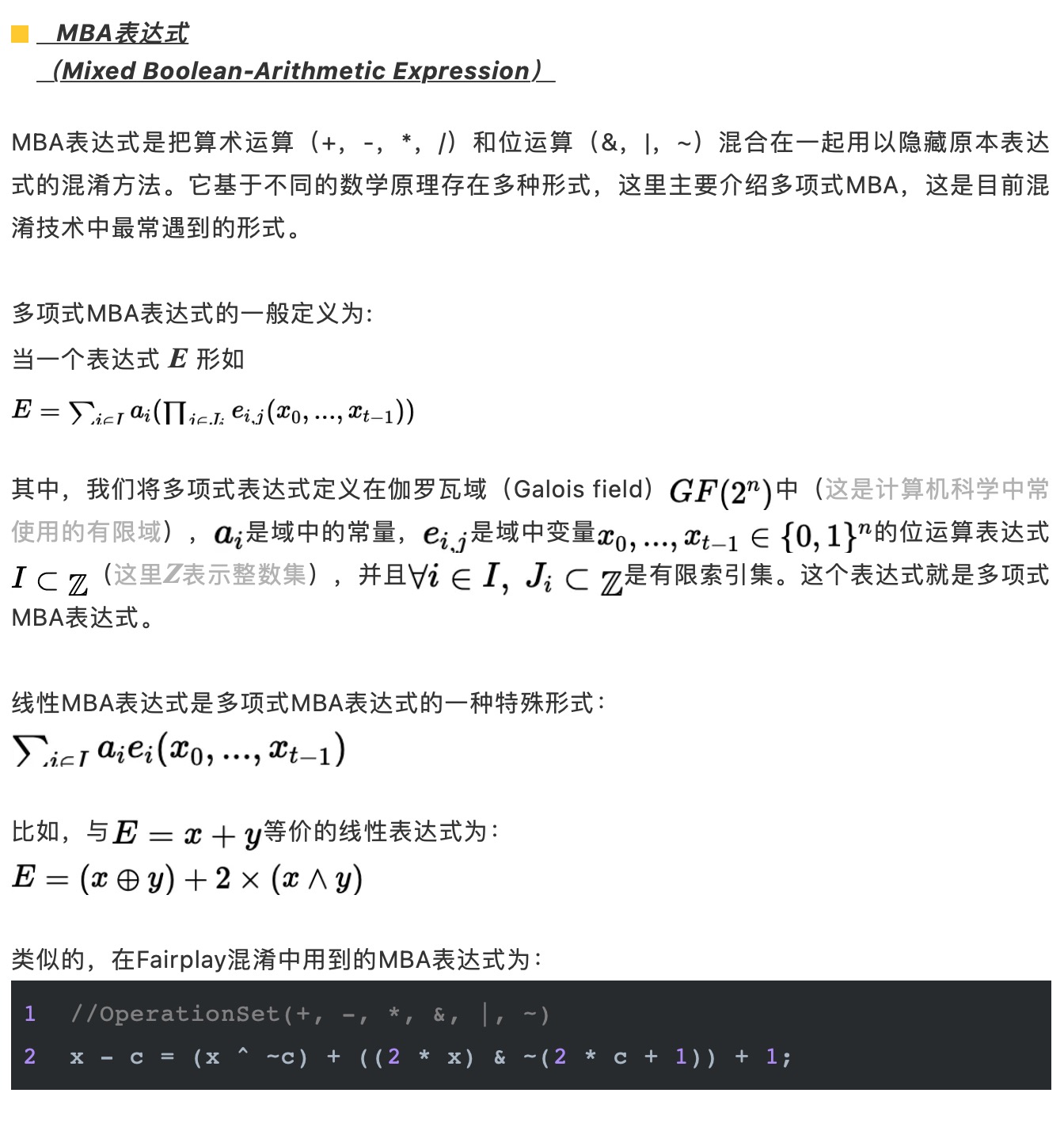

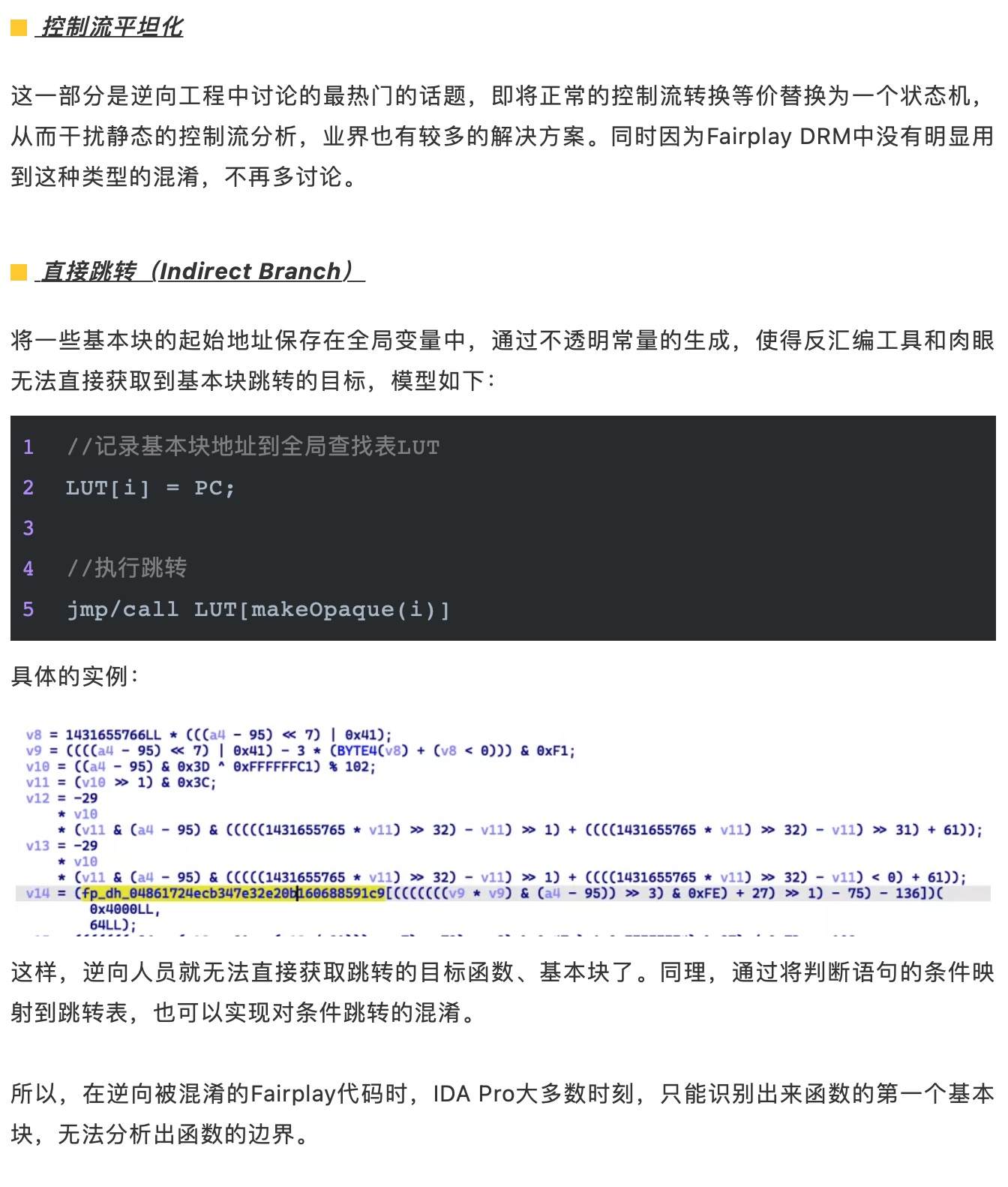



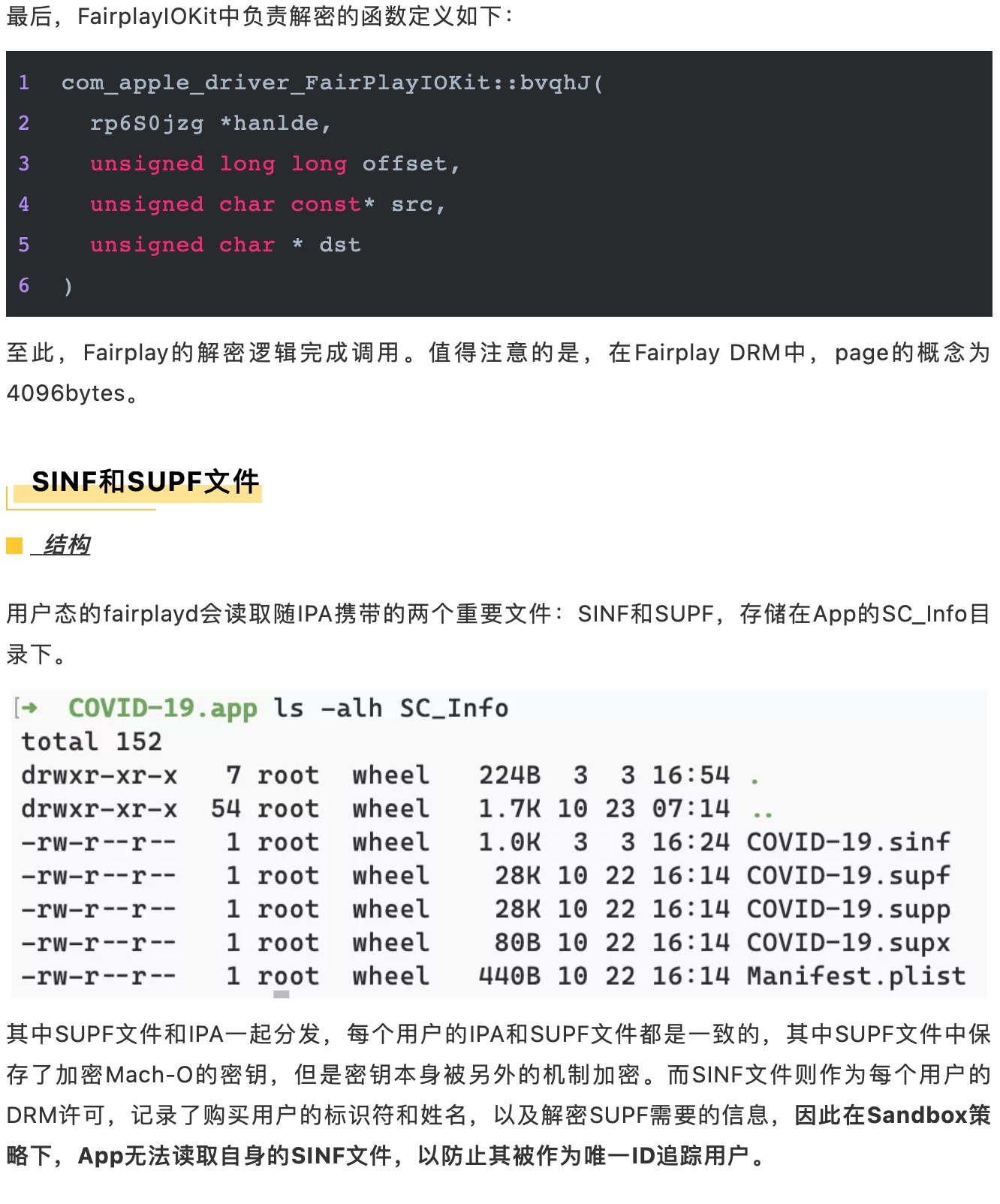
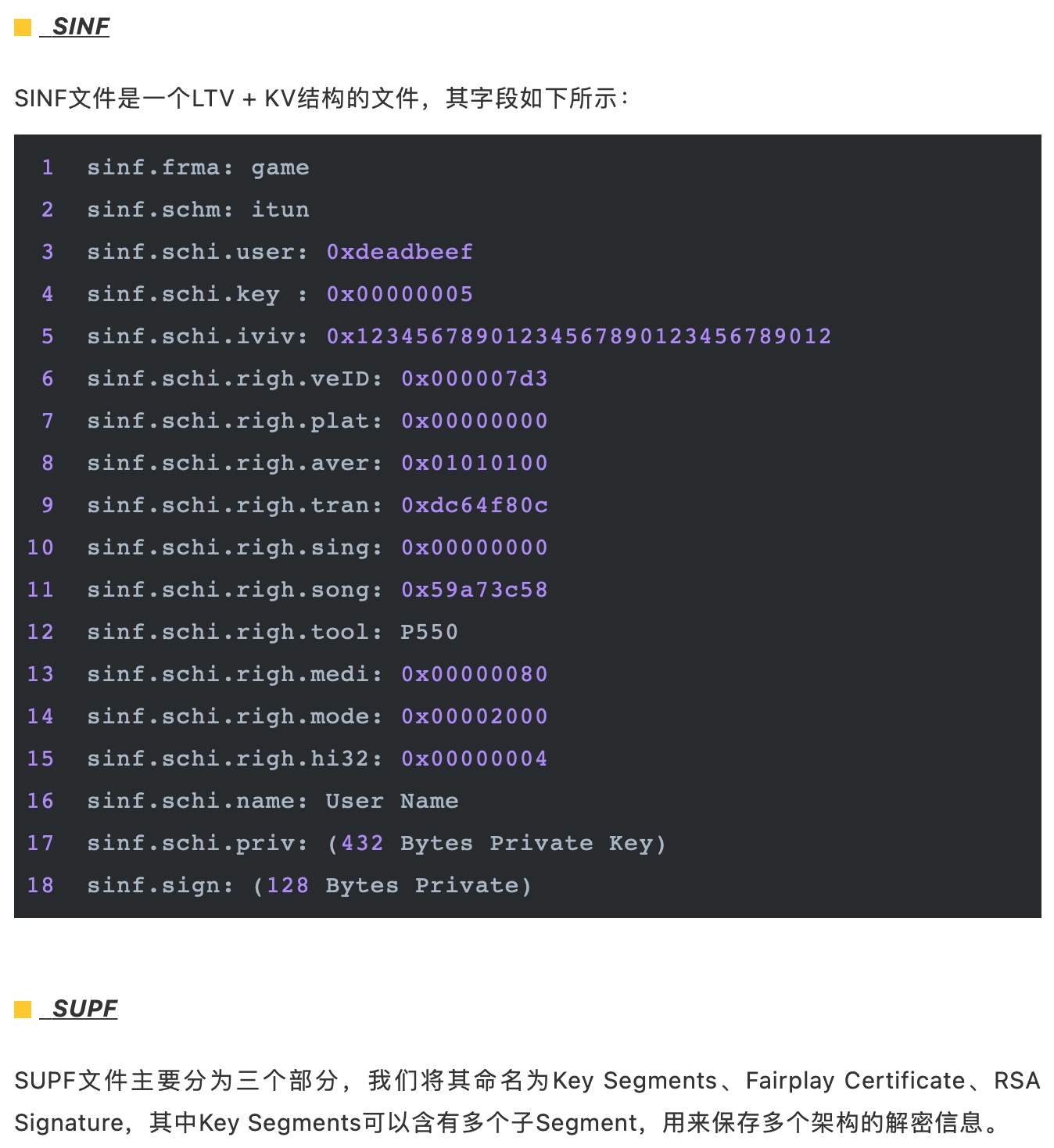
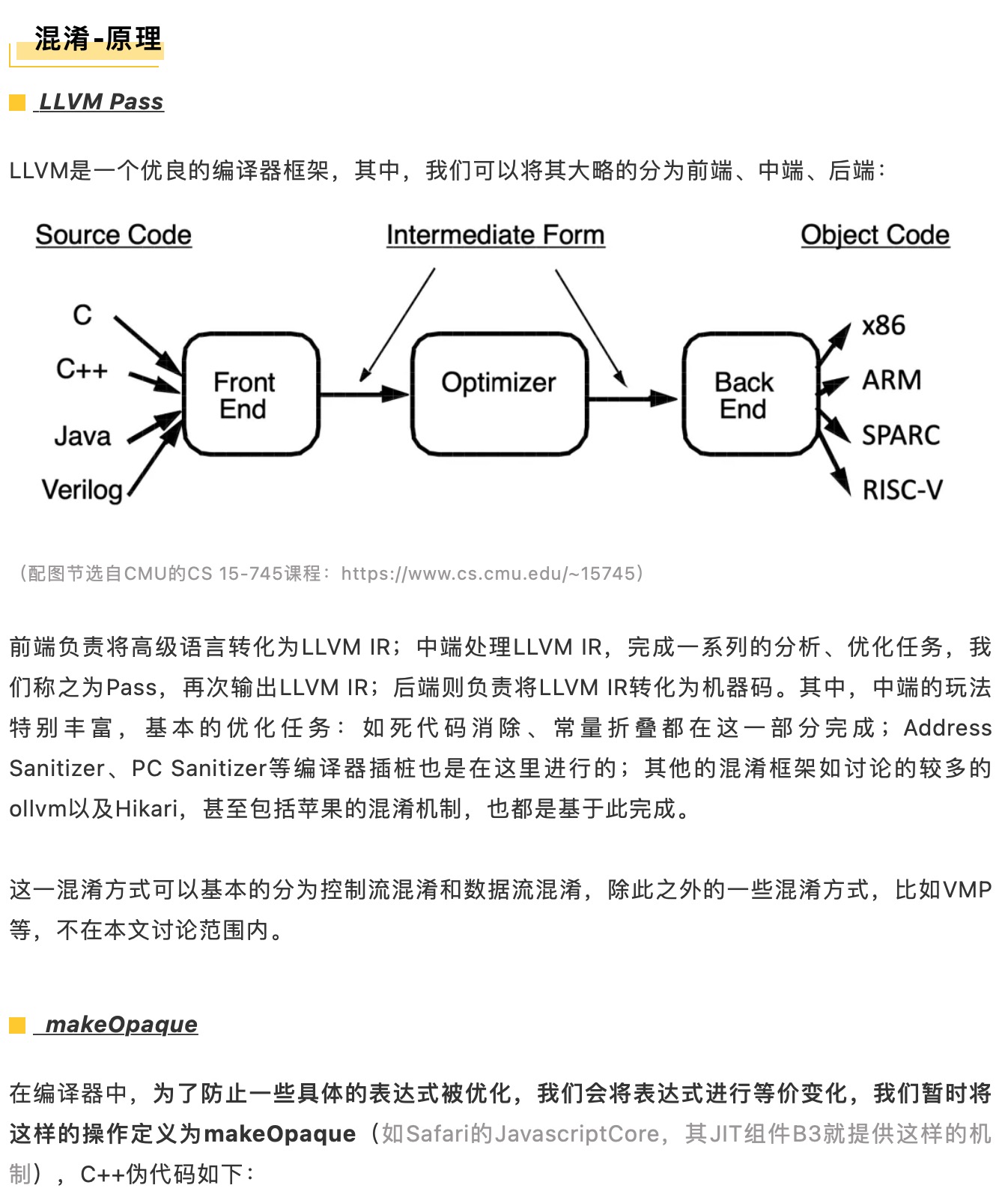
最后,附上源码地址,供大家参考和研究。
https://github.com/pwn0rz/fairplay_research

