My Journey To The Google Hall Of Fame
This is the story of the how Abartan Dhakal managed to get into the Google Hall of Fame, along a path strewn with failure and invalid vulnerabilities.

In this article I tell the story of the success I have had finding Google vulnerabilities, a success that is underpinned by LOTS of failure. This is the story of of how I turned my invalids into valid vulnerabilities and got into the Google Hall of Fame and hopefully will help you out during penetration test or during bugbounty hunting.
I have been trying to earn a seat in Google's Hall of Fame by finding at least one valid security vulnerability for a long time. I tried whenever I had free time at night (I have studies and work to do so don't ever get enough time for hacking).
After seven months of trying and getting my reports tagged as "intended behaviour of the application" or "won't fix", one incredible evening I was able to get my name into Google's "honorable mentions" and their "reward hall of fame".
This story is all about how Google themselves helped me find the vulnerability.
Note: This is not a super hack, merely a small Cross Site Scripting (XSS) vulnerability which was gained by exploiting open redirection.
Story Begins
I have been trying to find a valid vulnerability in the "Google" and "Youtube" domains with the hope of discovering some low hanging fruit. I had reported a few authentication related vulnerabilities with the hope of one being valid, but all those reports were invalid because the issues were 'intended' and did not poses any risk.
Then two months ago I thought to look into the acquisitions and I came across a new vulnerability, but sadly the report from Google also came back as invalid.
It was all a bit disheartening, after searching for so long I had found nothing but invalid vulnerabilities, so I had to stop, take a break and start learning a bit more.
So one fine day I was checking all the available proof of concepts that were there for Google's reports. At the same time, I found a site Sidewalk Labs . I first checkout out the application flow and at the same time was enumerating the subdomains.
Then as I was doing my recon, I thought of giving a Google dork shot to find some files and gain more attack surface, whenI came across this dork "site:*.sidewalklabs.com" and mistakenly pressed enter. I found a site "https://replicaexplorer.sidewalklabs.com" where there was a redirection parameter and checked that once you log in, you will be redirected to any website.
This was a sad moment because as per Google's VRP Open redirection is out of scope and therefore would not be rewarded. I then started checking for the available POC where Open Redirection could bring a big issue and I had completely forgotten about XSS till this phase.
Then I came across a post from google where a hacker had chained 3 Open redirections to get an XSS and hence Google had rewarded him a bounty. Then I started to find similar websites which might have open redirection.
But then suddenly, I came across a POC where Open Redirection was easily chained with "javascript:alert(document.domain);" to get XSS and without any time wasting, I tried this payload (had very less faith that it's gonna work because its "GOOGLE") and got amazed that it actually executed and gave me a sweet little Popup. I quickly made a report and within 13hrs they responded with a "Nice Catch!" response and within another 12days, I got rewarded.
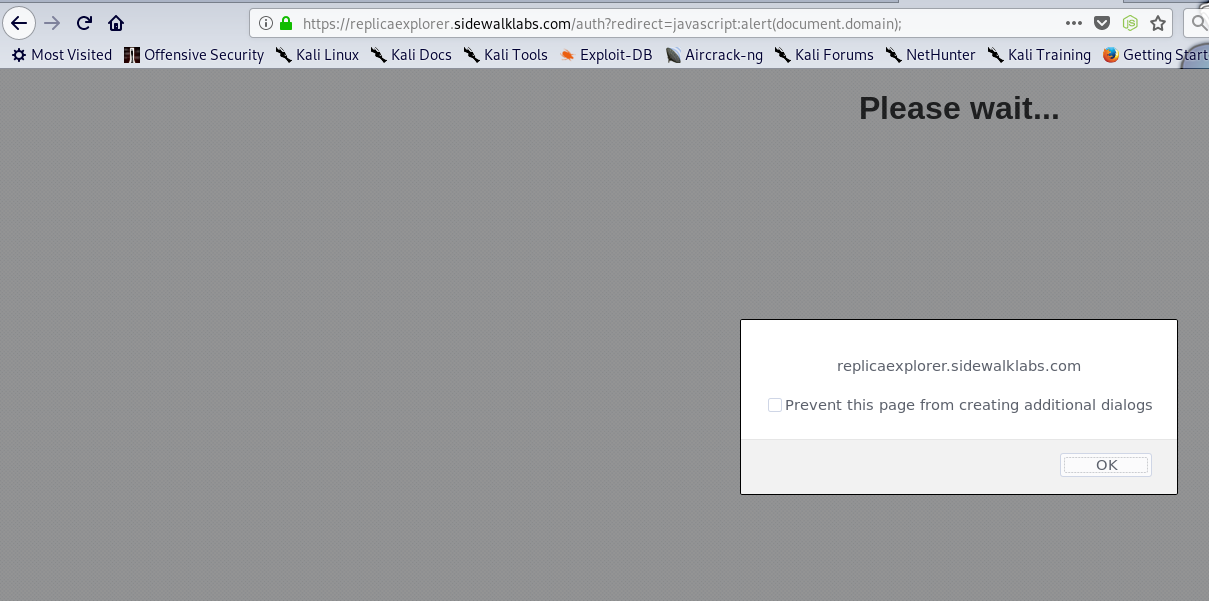
Quick Tips: If you want to hunt down big corps, try with their acquisions and never think if it's a very big corp then it won't have small vulnerabilities. Also even if you are hunting down Google, use help of google ;) (Google Dorking).
That was all. You can now find me on both hall of fames of Google here�.