| 信息源 | 时间 | ||
|---|---|---|---|
|
CVE
|
CVEnew | 原文
CVE-2022-21821 NVIDIA CUDA Toolkit SDK contains an integer overflow vulnerability in |
|
|
CVE
|
CVEnew | 原文
CVE-2021-43118 A Remote Command Injection vulnerability exists in DrayTek Vigor 2960 1.5.1.3, DrayTek Vigor 3900 1.5.1.3, and DrayTek Vigor 300B 1.5.1... |
|
|
CVE
|
CVEnew | 原文
CVE-2021-42911 A Format String vulnerability exists in DrayTek Vigor 2960 <= 1.5.1.3, DrayTek Vigor 3900 <= 1.5.1.3, and DrayTek Vigor 300B <= 1.5.1.3... |
|
|
CVE
|
CVEnew | 原文
CVE-2022-1122 A flaw was found in the opj2_decompress program in openjpeg2 2.4.0 in the way it handles an input directory with a large number of files... |
|
|
CVE
|
CVEnew | 原文
CVE-2022-1050 Guest driver might execute HW commands when shared buffers are not yet allocated, potentially leading to a use-after-free condition. |
|
|
CVE
|
CVEnew | 原文
CVE-2022-26514 Delta Electronics DIAEnergie (All versions prior to 1.8.02.004) has a blind SQL injection vulnerability that exists in DIAE_tagHandler.... |
|
|
CVE
|
CVEnew | 原文
CVE-2022-25880 Delta Electronics DIAEnergie (All versions prior to 1.8.02.004) has a blind SQL injection vulnerability that exists in DIAE_hierarchyHa... |
|
|
CVE
|
CVEnew | 原文
CVE-2022-26667 Delta Electronics DIAEnergie (All versions prior to 1.8.02.004) has a blind SQL injection vulnerability that exists in GetDemandAnalysi... |
|
|
Emad Shanab - أبو عبد الله
|
Alra3ees | 原文
Re @Bugcrowd @Six2dez1 ReconFTW @pdiscoveryio tools @KN0X55 @owaspamass @TomNomNom tools @BurpBounty @Sn1perSecurity @shmilylty oneforall @_maurosoria... |
|
|
Emad Shanab - أبو عبد الله
|
Alra3ees | 原文
Re @MohannadAbusai1 It’s recommended to check the results manually to avoid false positive results. Good luck. |
|
|
Emad Shanab - أبو عبد الله
|
Alra3ees | 原文
Re @0x_rood العفو. بالتوفيق ان شاء الله. |
|
|
Emad Shanab - أبو عبد الله
|
Alra3ees | 原文
Re @OriginalSicksec @hd_421 @wish_iwas Could you please tell me how and I appreciate it. |
|
|
Emad Shanab - أبو عبد الله
|
Alra3ees | 原文
Re @brinhosa You’re most welcome. |
|
|
Emad Shanab - أبو عبد الله
|
Alra3ees | 原文
Re @m4cvl_ @hd_421 @wish_iwas Yes brother. |
|
|
Emad Shanab - أبو عبد الله
|
Alra3ees | 原文
Re @starkcharry @hd_421 @wish_iwas Yes i know it and we use Femida to send xsshunter blind xss on all request and headers. You can use xsshunter burp ... |
|
|
DEF CON
|
defcon | 原文
Re @thesl3ep We can issue you a refund, and when you repurchase your ticket it will only include event name and location. |
|
|
DEF CON
|
defcon | 原文
RT Jorge: Re @masonic_tweets @Jason It's every hardware @ANDnXOR badge we made for @defcon . See some of our past work: |
|
|
DEF CON
|
defcon | 原文
RT SNOmad1 (☃️☃️.ml) (🏔,🏔) 让我们买一座山!: Re @Jason @defcon Best badges |
|
|
DEF CON
|
defcon | 原文
RT lamigs: Re @Jason @defcon has the best badges! |
|
|
DEF CON
|
defcon | 原文
RT givememalware is not dead, yet: I have a month to prep my submission for @Defcon's CFP. Will most likely need some input by some old timers (it wil... |
|
|
Black Hat
|
BlackHatEvents | 原文
Telegrip, a Python-based forensic tool aims to acquire & analyze sparse images, preserve evidence related to Telegram application while maintaining th... |
|
|
|
tombkeeper | 原文
要享受人类的崇拜,就得踏踏实实住在奥林匹斯山上。只要保持高高在上,你干什么都是对的。跟欧罗巴睡觉,放火烧索多玛,都是对的。人类会帮你找理由的,“天意从来高难问”,“上帝自有其行事之道”。可以“亲民”,不能真亲民。只要不是真亲民,就是“平易近人”。真亲民了,你就从神变成了Nephilim ...全文 |
|
|
|
yuange1975fuckwb | 原文
回复@wangjun2016111:前面那段是我转发别人发的,这明显算不上歧义呀,只能算口语化表达,很正常的表达。//@wangjun2016111:有歧义//@yuange1975fuckwb:真的是没有想到这么多人会认为打包120多是120多份。 |
|
|
|
yuange1975fuckwb | 原文
真的是没有想到这么多人会认为打包120多是120多份。 |
|
|
|
tombkeeper | 原文
renew |
|
|
|
祝佳音 | 原文
在知乎上看到一位狱警写的回答,说2020年1月开始,全国监狱系统进入封闭执勤状态。狱警执勤模式改为14+14+14,14天封闭隔离,14天封闭执勤,14天休息。个别人员不足的省份模式为14+28+14,即封闭执勤时间延长至28天。其中封闭执勤时不能带手机,相当于与世隔绝。回答者说,”六个循环下来,一年就过 ...全文 |
|
|
|
祝佳音 | 原文
好屌。这个大哥唱的是请神调,就是东北“跳大神”做法时萨满请仙家(一般包括狐狸、黄鼠狼、蛇或刺猬)上身时吟唱的曲调…… |
|
|
|
yuange1975fuckwb | 原文
「腾讯被吃穷了,终于限制晚餐打包了。之前有人晚餐打包太多,一人恨不得把全家人的饭都带回去。还有人5.10就去排队,打包完还要赶6.15的班车。现在规定一人只能打包一份,终于限制住羊毛党了。最多见一个兄弟,打包了120多的,马化腾看了都掉眼泪,还不如直接改回原来的夜宵券算了。不过好像现在不是 ...全文 |
|
|
renniepak
|
renniepak | 原文
Re @rez0__ @naglinagli Sir bro dude, invite write up share tips please. |
|
|
renniepak
|
renniepak | 原文
Re @naglinagli Pro tip. Love our (not yours) collective of "Sirs". |
|
|
renniepak
|
renniepak | 原文
RT Nagli: #1 Secret for for being a good #BugBounty hunter create a community of like-minded people to share your progress with. Since June 2021 Iv'e ... |
|
|
☣ KitPloit - Hacker Tools
|
KitPloit | 原文
LAZYPARIAH - A Tool For Generating Reverse Shell Payloads On The Fly |
|
|
Jenish Sojitra
|
_jensec | 原文
RT Corben Leo: Anyone can hack. Yes, anyone. You can hack. Big companies. With little to no technical skills. And make thousands of dollars. Legally. ... |
|
|
INTIGRITI
|
intigriti | 原文
RT CyberNews: To delve deeper into #BugBounty hunting, @CyberNews reached out to @StijnJans and @securinti, the CEOs at @intigriti, a bug bounty hunti... |
|
|
|
祝佳音 | 原文
很多孩子喜欢一个行业,不计代价地接近这个行业,心存幻想,美梦环绕,主动追求燃烧青春。有些人就是盯准这一点,自己取暖,让这些倒霉蛋成灰…… |
|
|
|
祝佳音 | 原文
看,现在同学毕业了吧……(我们不同,我们日常工作交流中会把广告客户尊称为”爹“,一种直面现实后仍然炽热朴素的情感。) |
|
|
|
祝佳音 | 原文
我觉得,将裁员称为 “毕业” ,和将同事称为 “同学” ,将穿着防护服的防疫相关人员称为 “大白” 其实是一脉相承的,对于资方而言是用粉色缎带包装冰冷事实,对于媒体或部分大于18岁的个人而言就是用粉色卡通滤镜过滤现实世界。 |
|
|
|
沈沉舟 | 原文
不要再在后台要burp,它就在那里,一直都在,但已与我无关。网页链接 |
|
|
|
yuange1975fuckwb | 原文
有上海的朋友让帮忙抢菜,我也不知道怎么帮着抢,看这么紧张,估计也很难有特殊渠道? |
|
|
|
yuange1975fuckwb | 原文
国外金融IT这烂的,1000股腾讯ADR现在还没看到分红,也不知道是怎么回事情。等到今天还没看到到账信息,终于忍不住问券商了。大陆这方面得甩他们地球到月球的距离了,第一天除权,分红、送股等很多晚上就到账了,迟的一般也是第二天早晨交易前就能看到。这次腾讯分红,两个多月到账,说25号到账结果 ...全文 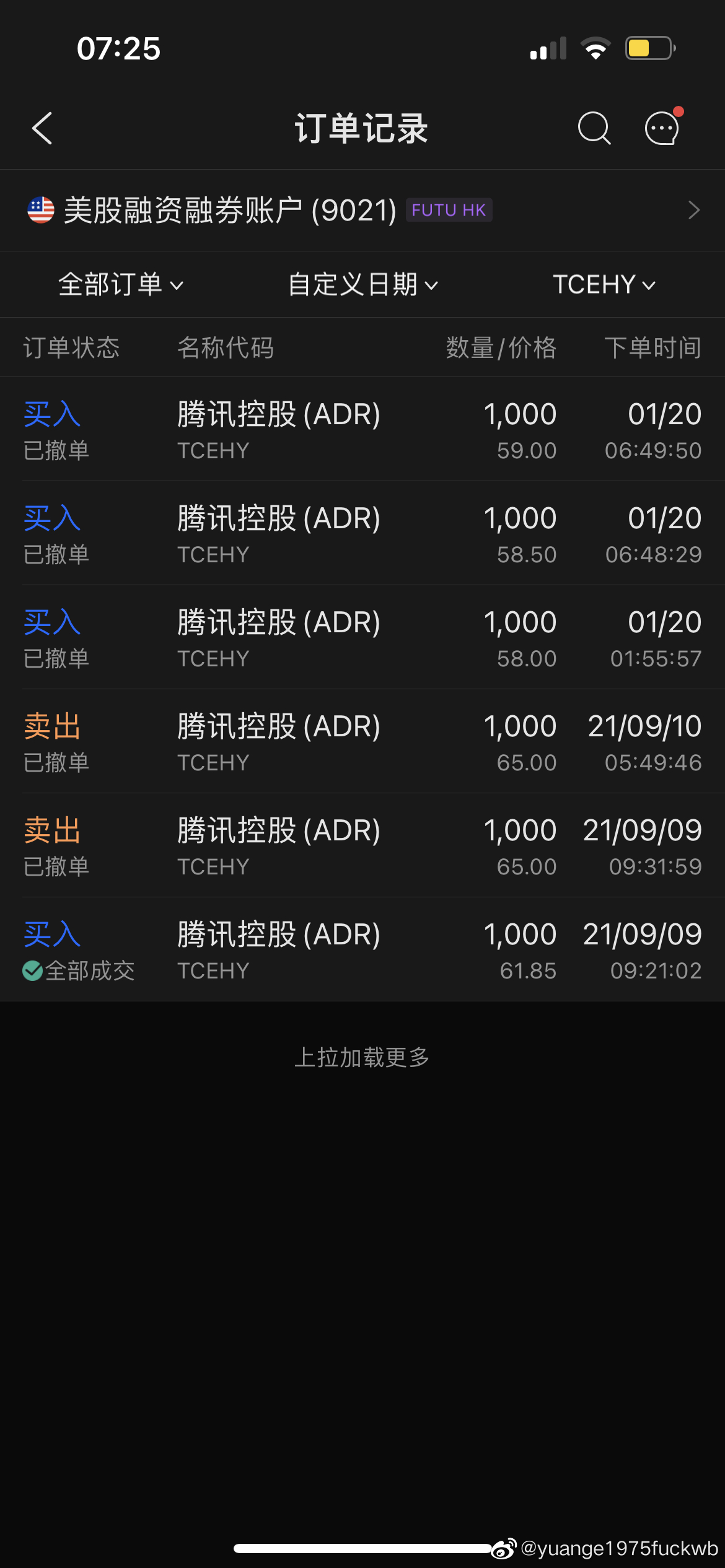
|
|
|
|
yuange1975fuckwb | 原文
看上海抢菜抢的,看来还是得回到原始社会,弄个院子自己种菜呀。 |
|
|
|
yuange1975fuckwb | 原文
动不动就核弹,哪有那么多核弹呀 
|
|
|
vx-underground
|
vxunderground | 原文
Yesterday @ESETresearch released a paper on a malware dubbed "WsLink". WsLink utilizes a custom built Virtual Machine. Not a VM for a hosting an OS, a... |
|
|
Elon Musk
|
elonmusk | 原文
Re @Teslarati @ResidentSponge I mean we’re basically identical – a few differences maybe … |
|
|
Elon Musk
|
elonmusk | 原文
Re @SawyerMerritt The UAW stole millions from workers, whereas Tesla has made many workers millionaires (via stock grants). Subtle, but important diff... |
|
|
Elon Musk
|
elonmusk | 原文
Re @SawyerMerritt UAW slogan – “Fighting for the right to embezzle money from auto workers!” |
|
|
Elon Musk
|
elonmusk | 原文
Re @gunsnrosesgirl3 “Don’t try this at home” |
|
|
NCC Group Research & Technology
|
NCCGroupInfosec | 原文
RT Cedric Halbronn: Hunting/exploiting for Pwn2Own Austin 2021 was fun, thanks @thezdi! Targeting a Western Digital NAS |
|
|
NCC Group Research & Technology
|
NCCGroupInfosec | 原文
RT Virus Bulletin: NCC Group has released a dataset of Cobalt Strike beacons (2018 - 2022) and a Python library called dissect.cobaltstrike for dissec... |
|
|
Phith0n
|
phithon_xg | 原文 |